The Group Law
The group law for elliptic curves states three points on a curve E sum to the zero (i.e., O = [0, 1, 0] at infinity in projective geometry). Let P, Q \in E, then the line through P and Q (if P=Q, then we use the tangent line at P) intersects E at another point R. The line through R and O intersects E at P + Q.
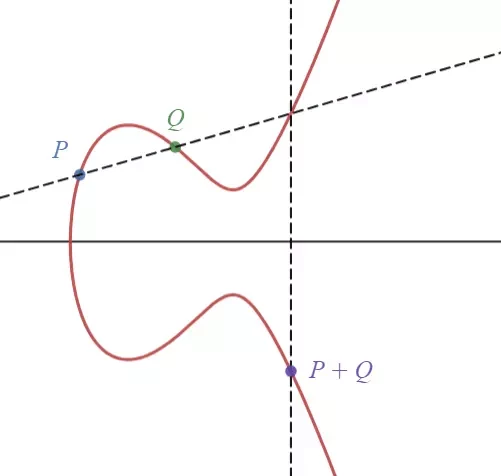
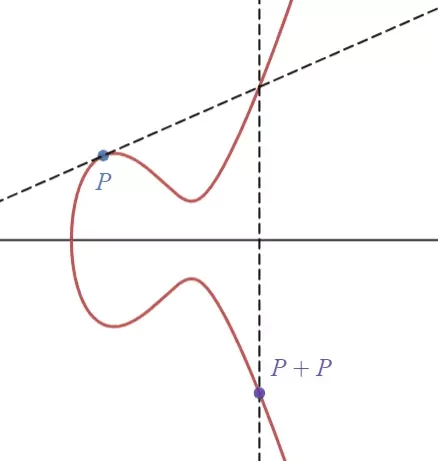
In this group, O is the identity element and the inverse of P=[x,y,z] is -P=[x,-y,z]. Note this group is abelian; in fact, this is the simplest example of an abelian variety. You may prove the commutativity and associativity by yourself.
Let n \in \mathbb N. We define [0]P = O, [n]P = \underbrace{P + \cdots + P}_{n\text{ terms}}, and [-n]P = -[n]P. We call n the order of P if it is the smallest positive integer satisfies [n]P = O.
Why Are ECC Keys Shorter Than RSA Keys?
Assuming G is a group and a,b \in G. Discrete logarithm problem (DLP) is the problem of finding x \in \mathbb N such that a^x=b. For any group, we need at most O(\sqrt{|G|}) steps to solve the DLP. The ease of solving DLP can vary among different groups. For example,
In the additive group of a finite field \mathbb Z/p, we can use Euclidean algorithm to solve the DLP in O(\log p) steps.
In the multiplicative group of a finite field \mathbb F_p, we can solve the DLP in \exp(c\sqrt[3]{(\log p)(\log \log p)^2}) steps (c is a constant).
In an elliptic curve E(\mathbb F_p), the best known algorithm solves DLP in O(\sqrt p) steps.
Because the DLP in an elliptic curve group is much harder, ECC keys are usually shorter than RSA keys.
Elliptic Curve Diffie–Hellman (ECDH) Key Exchange
Alice and Bob agree on a field \mathbb F_p, and elliptic curve E over the field \mathbb F_p, and a point P \in E(\mathbb F_p).
Alice selects a secret integer a and computes A = [a]P;
Bob selects a secret integer b and computes B = [b]P;
Alice and Bob exchange A and B;
Alice computes [a]B and Bob computes [b]A. Now they have the shared point [ab]P.
Elliptic Curve Digital Signature Algorithm (ECDSA)
Alice and Bob agree on a field \mathbb F_p, and elliptic curve E over the field \mathbb F_p, and a point P \in E(\mathbb F_p) of prime order N.
Alice selects a secret integer a and computes A = [a]P; this is her public key;
Alice randomly chooses another integer b \in [1, N-1];
Alice hashes her message and gets an integer d \pmod N;
Alice sets s_1 to be the x-coordinate of [b]P \pmod N;
Alice then computes s_2 \equiv (d+as_1)b^{-1}\pmod N;
Alice publishes s_1 and s_2;
To verify the signature, Bob computes v_1\equiv ds_2^{-1} \pmod N and v_2\equiv s_1s_2^{-1} \pmod N;
Bob then computes [v_1]P+[v_2]A; let g be the x-coordinate of this point. If Alice and Bob have the same message, then g \equiv s_1 \pmod N.
Elliptic Curve Encryption
Alice and Bob agree on a field \mathbb F_p, and elliptic curve E over the field \mathbb F_p, and a point P \in E(\mathbb F_p).
Alice selects a secret integer a and computes A = [a]P; a is the private key and A is the public key;
Bob randomly chooses an integer b. Assume the message Bob wants to encrypt is M;
Bob computes s_1 = [b]P and s_2 = M+[b]A;
Bob sends s_1, s_2 to Alice;
Alice obtains M by computing s_2-[a]s_1.
ECC is widely supported by modern browsers, operating systems, and cryptocurrency platforms. Compared with RSA, it's lighter and requires less computing power. Learning elliptic curve cryptography can enhance your understanding of modern cryptographic techniques.


